From Disillusionment to Productivity
“If you do not know history, you think short term. If you know history, you think medium and long-term.” ― Lee Kuan Yew
I originally intended to write more on Open Alchemy in 2022, but ended up taking a hiatus to focus on company-building and navigating industry-wide chaos.
I’m back. Readers can expect regular content uploads going forward.
--------------------------------------------------------------------------------------------------
Introduction
As 2023 opens on the heels of aggressive rate hikes, the end of a decade-long technology boom, and escalating global macro tensions, it’s difficult not to feel like we exist amidst a massive hangover in the aftermath of several euphoric years. This is true for markets at large and doubly true for crypto. It’s difficult to ignore how critical the capital environment of the past two years was to the industry. Inflationary policies left both institutional and retail participants flush with cash, a phenomenon that inevitably flooded into both private and public markets and led to the greatest boom the industry has seen in its 15 years.
Admittedly, a significant portion of this is now known to be transient. Gone are the days of absurd “risk-free” double-digit and triple-digit yields propped up by dangerous reflexive traps and mercenary capital looking to exploit short-term games. Gone are the days of pre-product protocols raising at nine or even ten figure valuations. Gone are the days of the minimal oversight that enabled reflexive traps such as Terra, overleveraged firm collapses like 3AC, and massively fraudulent systems like FTX. But as many of us contend with the aftershocks left by these implosions, it's impossible to deny that the same capital environment that enabled these setbacks also enabled maturation in many parts of the industry. Core DeFi protocols like Aave and Uniswap work and remain solvent throughout these crises. The launch of optimistic rollups and the shift to modular infrastructure are leading to exponential savings. Advances and investment in zero-knowledge proofs, multi-party computation, and other cryptographic primitives are bringing us closer to powerful privacy-compute platforms. There has been immense progress in these areas and more. But the events of 2022 have undoubtedly shown that there is much still lacking before the technology achieves widespread adoption and trust.
Pictured: ENIAC the first general-purpose, programmable digital computer completed in 1946. 77 years later, computers have solved problems previously thought intractable, but it took time, patience, and exceptional builders.
I won’t spend time detailing the events of the past cycle in detail; others have done that in great depth. Instead, I find it more productive to inquire first principles of what we’ve done well and which trends will arise as a consequence. To do that, we frame a few simple questions.
--------------------------------------------------------------------------------------------------
What has crypto proven better at than existing technologies and systems?
Resource Aggregation and Coordination
The architecture of blockchain networks combined with the prevalence of token-based protocol economies inherently lower barriers to resource management and allocation. Traditional economic and technological systems typically face fragmentation at the architectural level, so much so that reducing frictions in payment networks and developing APIs for communication between financial institutions is a multibillion-dollar industry in and of itself. On the other hand, applications built on cryptonetworks inherently benefit from composability and frictionless transfer. The use of token standards like ERC20 and ERC721 as units of financial value and data simultaneously enshrines interoperable logic and allows for greater programmatic flexibility between applications built on cryptonetworks. Likewise, wallets as the primary interface for the custody and management of tokens simplify the experience for end users. The result is a highly fluid experience, in contrast to traditional systems that usually require users to have multiple accounts for different applications and slow payment or communication networks between them. As a consequence, it becomes very easy to aggregate resources for new applications. Examples include Uniswap’s open-ended liquidity provision model providing deep liquidity depth that enables it to be competitive to CEXes or the use of NFTs by brands like Kith and Nike as universal access passes for tailored drops and services. It is important to caveat that this has largely extended to chains/rollups sharing VM-equivalency, but with generalized interoperability protocols like LayerZero and Axelar, this is rapidly encompassing chains with different VMs as well.
Transparency, Openness, and Codified Laws
While opponents of crypto may snicker and make tongue-in-cheek remarks about crypto’s so-called “transparency and openness” in light of 3AC, FTX, and DCG, it’s important to note that these institutions were organized as traditional, centralized financial institutions that happened to deal in cryptocurrencies and related assets as the underlying currency. Instead, when I refer to transparency and openness, I’m referring to applications and protocols built on crypto rails. Applications built primarily on blockchain infrastructure with crypto principles in mind must necessarily use smart contracts for most functionality and asset management, which enshrines visibility into the application's operations down to the code. As a result, such applications must also necessarily be designed to be trustless and permissionless, which entails codifying rules related to the governance and risk management of the application within contract functionality. This is incredibly powerful; we’ve already seen that Alameda repaid its loans to DeFi protocol Abracadabra to avoid programmatic liquidation before any other outstanding FTT-related liability. At any given time, a user can check the financial health of a protocol like Compound or verify that royalties from an NFT project are going to a treasury address where funds are not being misappropriated.
Protocolization, Ownership, and Open Development
Applications built on blockchain rails benefit from being protocols first. Having permissionless programmatic access to core features via contracts combined with composability via token standards means that each application can serve as a powerful primitive on which other applications can be built. Furthermore, as protocols move towards decentralized governance via DAOs, protocols typically issue tokens to users through various schemes that provide them ownership of the protocol. The combination of a sense of ownership and governance rights over things like treasury allocation potentially incentivizes users to expand on the protocol to increase the value of their stake and to allocate to external projects that do so as well. This community-led development of a protocol can help on-chain applications expand into categories and markets far more quickly and creatively than the core team would be able to on their own. Prominent examples of this include the suite of automated LP management and options projects built on Uniswap V3, NounsDAO funding of everything from luxury glasses to pseudonymous forums, and of course, projects like Gitcoin and Immunefi powering open-source protocol development and security.
--------------------------------------------------------------------------------------------------
What are the significant barriers to the adoption of crypto?
Transaction Costs
Virtually all blockchains implement some sort of dynamic fee market to determine how resources get allocated. This, combined with users generally having a time preference on transactions, lead to a suite of phenomena that can make a transaction on blockchains very expensive, including MEV. Leo Zhang and I studied the explicit and implicit costs involved in using blockchain networks in-depth and demonstrated examples during various market events. High fees can make blockchain networks entirely unusable save for a select few, which is antithetical to their purpose. Furthermore, phenomena like toxic MEV can impact the user experience in more subtle ways, such as adversely affecting the price of execution for unsophisticated market participants. Mitigations to MEV have been made via innovations in resource pricing (i.e. EIP-1559, EIP-4844), protocols aiming to minimize the externalities of MEV (i.e. Flashbots, Bloxroute), and, most importantly, attempts to scale both transaction throughput and the availability of blockspace without significantly sacrificing security via infrastructure modularization (rollups, DA layers, etc. Solving these bottlenecks is crucial to ensuring that crypto can scale in a way that encourages adoption, even from less sophisticated users.
UX, Trust, and Security
The same architectural components and principles that benefit crypto-based applications can sometimes prove to be a double-edged sword. While wallets, smart contracts, and tokens prove to be powerful tools for composability, they also provide attack vectors for malicious vectors. These include everything from contract-level security exploits to seed phrase phishing to blind signing transactions. Many of these security exploits can be attributed to two factors. First, a large majority of exploited protocols and applications are unaudited. Getting quality audits can often take several months due to the immense backlog for auditors and capital constraints. Furthermore, audits are not a catchall as some vulnerabilities may go undetected. Second, many self-custody solutions utilized by end users still rely on seed phrases for private key recovery and do not provide services to understand what users are signing. Exploits related to these issues come at a great financial burden (Immunefi estimates nearly $4B in losses from hacks and fraud/scams in 2022) and erode consumer trust. Until we have suitable solutions to these core issues, user adoption of crypto will be difficult.
Longevity and Effective Governance
As many protocols and applications shift to governance via DAOs and token systems, the tradeoff between speed and decentralization is clearly felt. Traditional companies are able to move fast and benefit from hierarchical structures, where the decisions of a few individuals set company-wide changes. Everyday decisions on specific subject areas are left to individual teams and larger strategic decisions are left to a management committee and/or a board of directors. With most current DAO implementations, we see that this is not the case: the same token that is used to vote on proposals for new product developments is used to vote on small code changes. This sort of governance structure makes it incredibly difficult for any application or protocol to move fast and quickly without a highly engaged set of stakeholders. Other market factors may also lead to easy governance Sybil attacks or other circumstances that can severely impede the longevity of protocols. If crypto is to expand, it must incorporate both principles from traditional corporate governance and innovations that reflect the powerful capabilities of smart contracts.
--------------------------------------------------------------------------------------------------
What emergent trends can we expect as a consequence?
In light of the strengths and barriers outlined above, we move towards discussing what innovation we might expect to arise as a result.
--------------------------------------------------------------------------------------------------
Prevalence and Operationalization of the Modular Stack
Two years ago, Charlie Noyes and Dan Robinson compared Ethereum’s existing (monolithic) architecture to mainframe computing, in contrast to the Cosmos ecosystem, which they believed was more akin to a protocol for building and networking between independent servers (thanks to Cosmos SDK and IBC). I find this comparison to be fair and likely true. While there has been some fantastic work done on scaling monolithic chains, it’s clear that most eventually run into the bounds of the scaling trilemma. Ethereum, while secure and decentralized, can become prohibitively expensive during times of high load. Solana has historically been less decentralized and had its own share of security problems. There are some interesting chains working on continuing to improve upon this model (i.e. Aptos, Monad, Sui), but it’s likely they too will run into similar issues.
Cosmos, on the other hand, makes it easy to spin up application-specific chains, thus making it easy to create more blockspace tailored towards scaling specific tasks. However, being able to spin up a new validator set for each new chain is not trivial and can often compromise decentralization and/or security. As a result, we see the same sets of validators acting across various different Cosmos chains. Additionally, individual Cosmos chains might still eventually face the same issues that have challenged other monolithic chains. Nonetheless, Cosmos presents a promising vision for how we might scale application development and blockspace production in crypto. There are also some interesting visions for security including the very topical Interchain Security and Mesh Security (I particularly like Sunny Aggarwal’s NATO analogy).
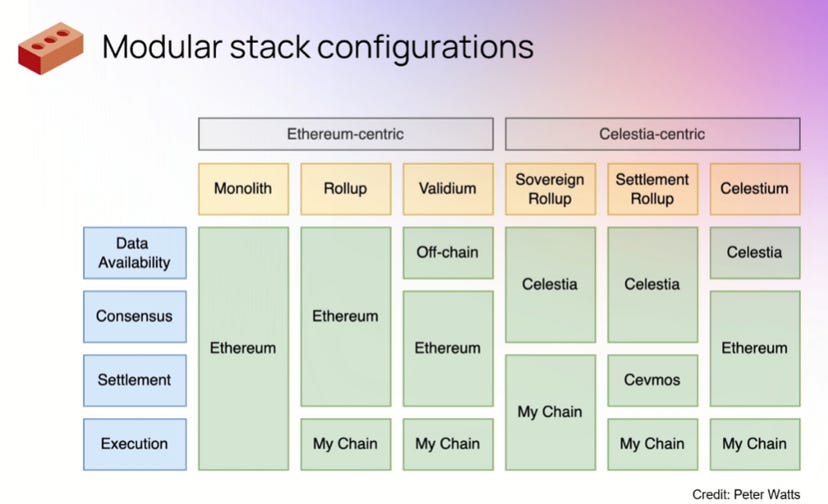
An alternative way to consider the scalability trilemma is to look at it through the lens of resource pricing and blockspace. In traditional monolithic chain architectures, the storage of historical chain data (data availability layer), the execution of application logic to advance chain state (execution layer), and the secure settlement of state (settlement layer) are all done by the same nodes. This can make interacting with chains expensive since the resource provisioners are non-optimized. The modular chain stack instead separates these layers, typically having infrastructure dedicated to each individual layer. This enables nodes participating in the upkeep of each layer to be far more specialized, leading to exponential cost savings. An example of this would be an application built on a zk-rollup like zkSync getting executed (zkSync is the execution layer), where the sequencer data for the rollup gets posted to Celestia (a data layer solution), and the proof generated to show a valid state transition is submitted to Ethereum to be included in a block (the settlement layer; zkSync is borrowing Ethereum’s security for settlement). This leads to >100x cost savings over an application that exists on Ethereum and uses Ethereum for all three layers. Execution layers benefit from being able to borrow the security of a settlement layer via validity or fraud proofs and can save in cost by posting their data to a dedicated DA layer.
Examples of modular stack configurations using Ethereum and Celestia. Credits: Celestia
As mentioned, transaction costs are an immense burden on crypto. I believe a world in which transaction costs are low enough to no longer impede adoption is better facilitated by modular architecture. To this end, we can expect a few things.
First, a few layers with high security and decentralization will compete as settlement and DA layers. Because decentralization of the underlying validator set of these layers is critical, the chains that are able to compete are those that will be able to have the largest (unique) validator set. Key players in the settlement arena will be existing chains that meet these conditions (i.e. Ethereum) or new chains that are successful in optimizing for settlement and can bootstrap similar validator sets. Key players in the data availability space so far are Celestia, EigenDA, Polygon, and Ethereum,
Second, there will be a bevy of Rollup-as-a-Service (RaaS) companies that offer easy-to-use SDKs for spinning up and designing custom rollups that will monetize by provisioning their own settlement and/or DA layer, or revenue share agreements with another DA/settlement layer. These services will differentiate themselves on the basis of specific VM capability, optimization for certain application types (i.e. gaming), and network effects stemming from other rollups in the specific RaaS companies' network. Key players in the RaaS space so far include Eclipse, Constellation, and Argus.
Finally, there will be heavy competition among execution layers, and it will get commoditized and/or increasingly app-specific. Perhaps the most self-explanatory, we will see execution layers attempt to compete on the basis of cost, ecosystem development, product offerings, finality, privacy, and other features. There are numerous big players here so I’ll name some of the most popular: Optimism, Arbitrum, Scroll, zkSync, Starkware, Aztec, Fuel, and the execution layers powered by the RaaS platforms mentioned in 2.
The modular stack thesis powered primarily by Ethereum and Celestia will come to dominate infrastructure, with Cosmos lagging a good bit behind, and monolithic chains lagging the furthest. In the future, I think that monolithic general-purpose (non-app chains) will attempt to bootstrap ecosystem funds and incentivize execution layer development in the same way they attempted to incentivize protocol building this cycle.
--------------------------------------------------------------------------------------------------
Restaking
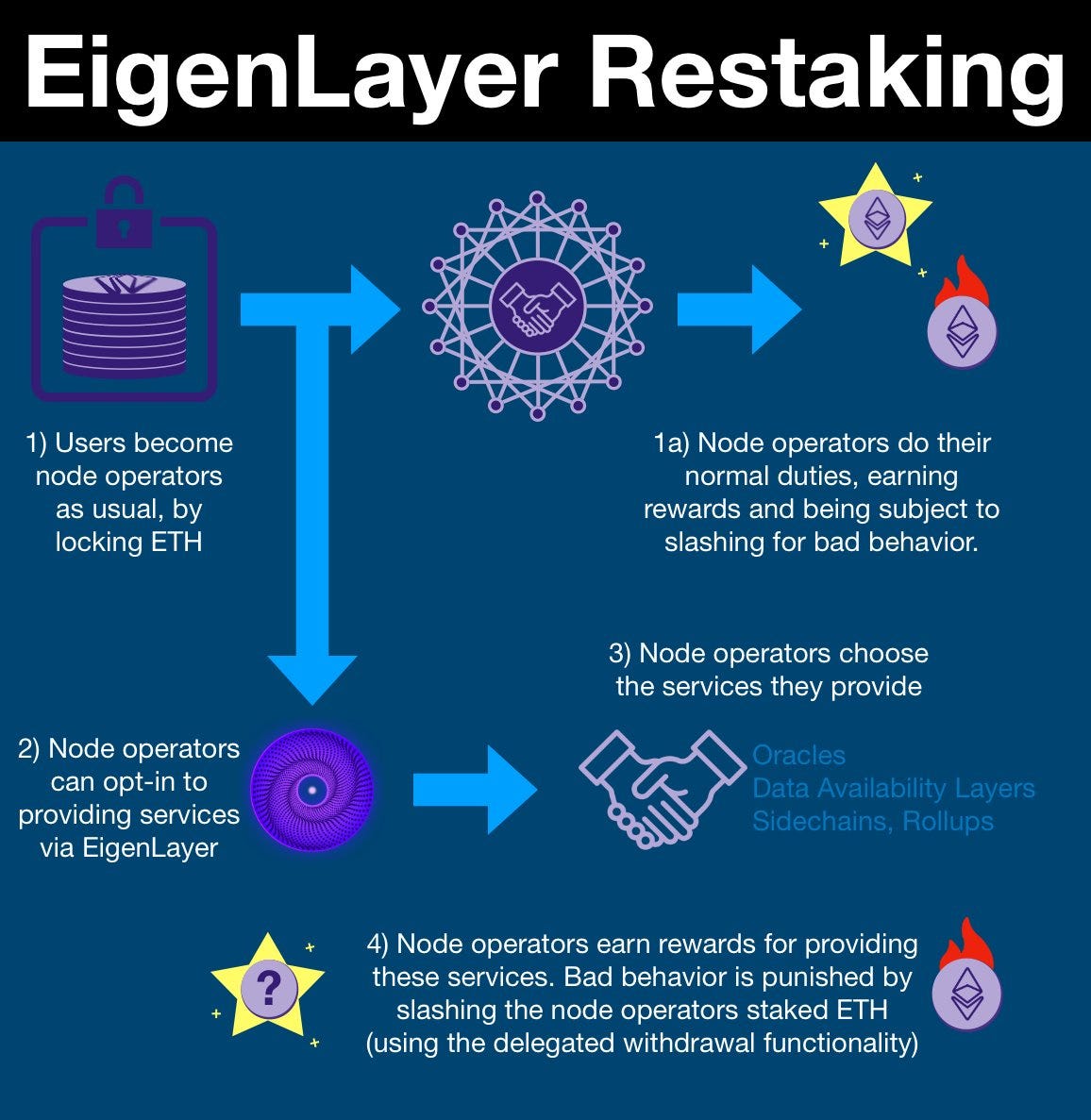
While the idea of borrowing the security of a settlement layer like Ethereum is a potent way to attach security guarantees to execution layers, it turns out that this same security can be leveraged in other manners. In particular, Proof-of-Stake (PoS) systems codified on-chain can be expanded on via restaking, which involves using nodes and their stake within an existing PoS network to validate other networks and applications, with penalties leveraged by slashing some fraction of the stake, In other words, an Ethereum or Osmosis validator would be able to use its stake to secure a Chainlink oracle and be rewarded for doing so.
The restaking process with EigenLayer. Credits: EigenLayer
Restaking is a powerful concept that offers new chains and applications to borrow the security of existing networks very quickly. In turn, validators on networks can rehypothecate their stake and diversify revenue streams by opting to restake for services. However, it is worth noting that restaking does require nodes to support the additional computational and storage requirements for the services they opt into. This is significantly less concerning for applications with low resource requirements (i.e. securing oracles), but for applications that are resource intensive (i.e. restaking to secure another chain or for DA) it can lead to increased hardware requirements. This inherently constrains the set of validators that can opt into these heavier-load services and potentially lead to centralization.
Nonetheless, restaking provides a powerful toolbox for middleware applications that were previously hard to secure (oracles, bridges, etc.). The most significant player in this space is EigenLayer. Additionally, there have been talks of using restaking dynamics for interchain security in the Cosmos ecosystem, but nothing has yet to come to fruition.
Restaking will become ubiquitous for chains, particularly for securing middleware, within the next few years. There is a likely future in which pieces of infrastructure like oracles and bridges become enshrined in consensus (or some subset of consensus) via restaking, due to the higher security offered. Restaking will see limited success in computationally intensive or stateful applications and might be better utilized as a method to bootstrap applications prior to bootstrapping their own validator security. Restaking might also help curtail the long-tail distribution of validator rewards, as smaller validators will be more willing to restake and take on the risks of maintaining external networks to compensate for the lower revenue from core consensus. However, the opposite is also true. Bigger validators that are willing to restake can compound rewards from restaking to continuously acquire more ETH (or whatever consensus token) and thus crowd out smaller validators. Managing the balance will likely be an important point of security and risk management.
--------------------------------------------------------------------------------------------------
Scaling Audits and Security
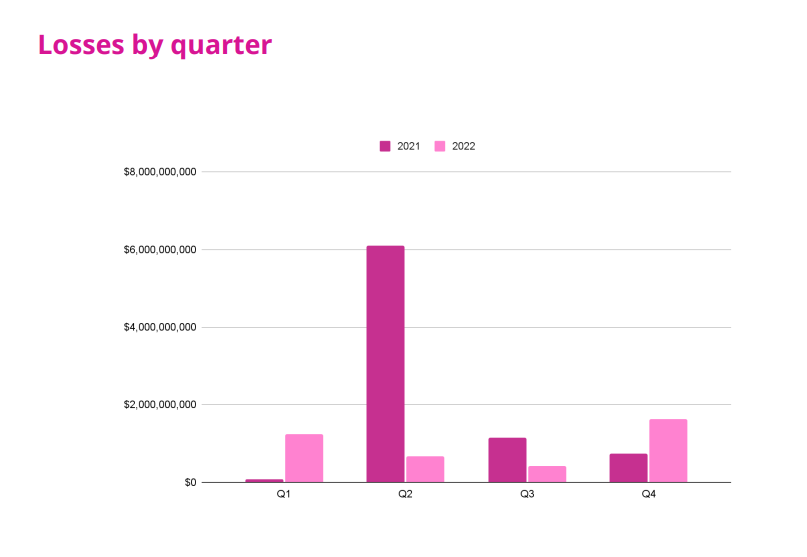
In 2022 alone, Immunefi reported that just over $3.9B was lost to hacks, fraud, and scams (this does not include FTX, 3AC, or Luna/UST). In 2021, that number was $8B. Of that $3.9B, $3.7B was due to security exploits, with 80.5% of those exploits being in DeFi and the rest in CeFi (similar patterns can be observed for 2021). Clearly, on-chain protocols are disproportionately affected by security exploits and account for a large portion of funds stolen from the ecosystem.
Losses due to exploits and fraud in 2021 and 2022. Credit: Immunefi
Exploits like the ones detailed in the Immunefi report erode consumer trust in the crypto ecosystem. After all, no one wants to deposit their money in an institution that could get drained by a malicious third party, with little to no recourse (only 5.2% of funds from exploits were returned). Furthermore, most protocols that do get hacked also tend to be unaudited. Protocols that undergo even a few audits have a drastically lower chance of getting exploited. If crypto is to fully realize adoption, consumers and institutions must feel secure about the platforms they use. A world in which protocols are audited frequently, and have measures for continuous monitoring to minimize forward exploit risk, is one which fosters consumer confidence.
However, getting an audit is difficult. The process originates by contacting an established auditing firm like Trail of Bits or OpenZeppelin and securing an audit contract. There is a tremendous supply-demand imbalance between projects demanding auditing services and competent firms able to deliver. This manifests in long waitlists which impede project timelines/deliverables. Consequently, many elect to launch unaudited, which poses significant risks.
If crypto is to scale, then the processes by which projects are able to get security coverage must also scale. This happens in a few ways:
Audits become commoditized and decentralized via a combination of audit and bug bounty marketplaces and DAOs formed by competent white hat hackers that build their reputations. Platforms like Immunefi and Code4rena provide infrastructure by which projects are able to openly post bug bounties and requests for audit, which anyone can choose to take a stab at in exchange for rewards from that project. In contrast to the centralized audit model which requires contracting a specific organization, these platforms help open up the security coverage process to anyone, with oversight being provided by impartial, expert auditors. Similarly, DAOs like Pwnednomore can provide effective interfaces for individual white hat hackers to get contracted. DAOs, in comparison to centralized audit shops, have the additional flexibility around personnel allocation and compensation (individual auditors can join multiple DAOs, and get compensated in accordance to only that which they worked on), and can help broker bug bounties for their members. In conjunction with both security marketplaces and hacker DAOs, we might expect a robust reputation layer to emerge around individual auditors/groups that help them garner the same level of trust as established firms (we already see this happening with individuals like samczsun). Key players in this space are those that were mentioned here; Immunefi, Code4rena, Spearbit, and Pwnednomore.
Audit firms will continue to rely heavily on technologies that expedite the audit process without compromising audit quality. Specifically, increased reliance on and usage of formal verification, static analysis, and agent-based models/ML (or a combination of the above) will help drastically increase the throughput of auditing firms. Most big auditing firms already use these technologies and are looking into developing them further; additional key players are Pwnednomore (with their SKOLL platform) and Veridise (which offers these technologies as a service, along with their own in-house auditing services).
Lastly, continuous oversight will be key. It’s important that users know which projects and codebases have not been audited, and for projects to have continuous, ongoing security coverage while in production. Two key players here are Zellic, which launched a tool for tracking audited codebases, and Forta Network, which hopes to create a decentralized network of ML agents for continuous contract oversight.
The auditing industry will transition into a much more fluid system buoyed by reputation management and marketplaces. We will still have a somewhat long tail distribution in the quality of audits that favor larger firms, especially in a cycle that’s likely to see lower urgency for audits and deployment timelines. However, as core security technologies become more ubiquitous and accessible to smaller auditor groups via platforms like Veridise, we will start to see more DAOs like Pwnednomore seriously compete with large established firms.
--------------------------------------------------------------------------------------------------
Consumerization of OpSec
While exploits against large protocols make up for the lion’s share of lost funds in crypto, a non-negligent amount is also lost via attacks taking advantage of poor consumer OpSec (operations security). There are many vectors here: blind signing, seed phrase phishing, etc. are all areas the average consumer is not aware of (after all, phishing works in much less complicated environments than crypto). The reality is, understanding private key management is difficult, as is proper security management around seed phrases. To this end, the burden of OpSec will fall on those building products.
MPC (multi-party computation) wallets and social recovery wallets will supersede the seed phrase model. Wallet activity has traditionally been dominated by Metamask, which relies on the traditional seed phrase and private key model. But such wallet architecture is not necessarily consumer friendly and exposes several points of failure (i.e. seed phrase phishing). MPC wallets split up user private keys into individual secrets that get distributed to multiple holders; MPC then allows transactions to be signed only if these secret holders sign it together. This reduces single points of failure by ensuring that no one agent knows the private key to a wallet. Somewhat similarly, social recovery wallets typically have a single signing key to approve transactions, with a set of external guardians (who do not need to have the same wallet type) that can change the signing key. This way if the main signing key is compromised, guardians can take over and change the signing key to an uncompromised public address. Social recovery wallets are typically implemented as smart contracts, which means even more functionality can be baked in for security. An example would be implementing daily transfer limits as a form of a circuit breaker. Key players in the MPC wallet space include ZenGo, Fireblocks, Coinbase Wallet, and Marble. Key players in the social recovery space include Argent, Waymont, and the Loopring Wallet.
We will also see more firewall solutions that offer in-the loop-protection. While improving wallet security is a good way to improve opsec in a consumer-friendly manner, there still remain a number of hacks, scams, and thefts that users can fall for. To this end, I believe that users will be able to opt into firewall services that can block transactions outside user-defined trusted networks, scan and detect malicious transactions, and/or move funds to on-chain vaults before hackers can drain wallets. This will either come through custodial vaults that funds get transferred into before they can be drained (via MEV) or even more base layer applications, such as an RPC provider that scans and blocks potentially malicious transactions. This will help users gain peace of mind by offering both proactive and retroactive protection. Key players in this space are Blowfish and Harpie.
While wallets like Metamask and Phantom remain the dominant hot wallets, the ease of use for less sophisticated participants will propel MPC wallets and social recovery wallets to the forefront. , Both retail and institutional users will be willing to compromise on the trust tradeoffs of systems like Harpie, for increased recovery recourse in event of a hack.
--------------------------------------------------------------------------------------------------
Stablecoins and Other Real-World Assets
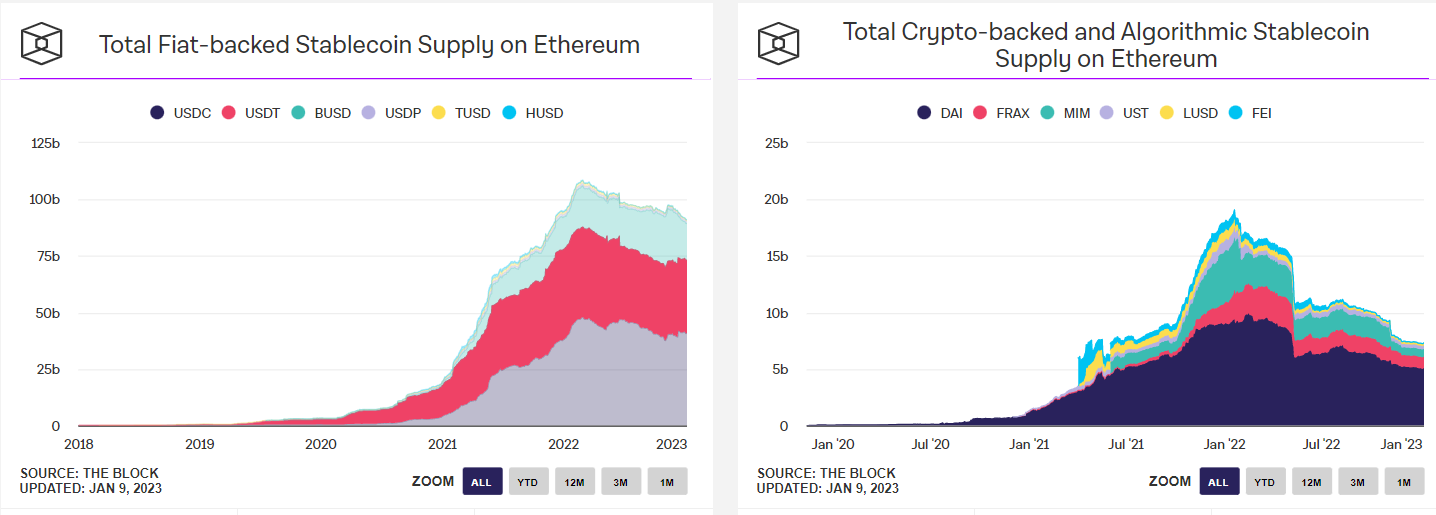
Stablecoins and other real world assets (RWAs) have occupied significant mind share for a while now. Some of the largest companies and protocols in the space (i.e. Circle and MakerDAO) have been built on creating on-chain assets pegged to the U.S. Dollar and other currencies, with solutions ranging between centralized custodians minting assets on-chain to crypto-backed and algorithmic approaches. Indeed, stablecoin growth has been tremendous over the past few years, and the deepest liquidity pairs on DEXs are usually stable-related pairs. There are even protocols, like Y2K Finance to insure against depegs. There’s not much to be said on stablecoins that hasn’t already been extensively studied. Key players in the space are the typical suspects: Circle, MakerDAO, Frax Finance, Tether, Binance, and Abracadabra.
Stablecoin supplies on Ethereum. Credit: The Block
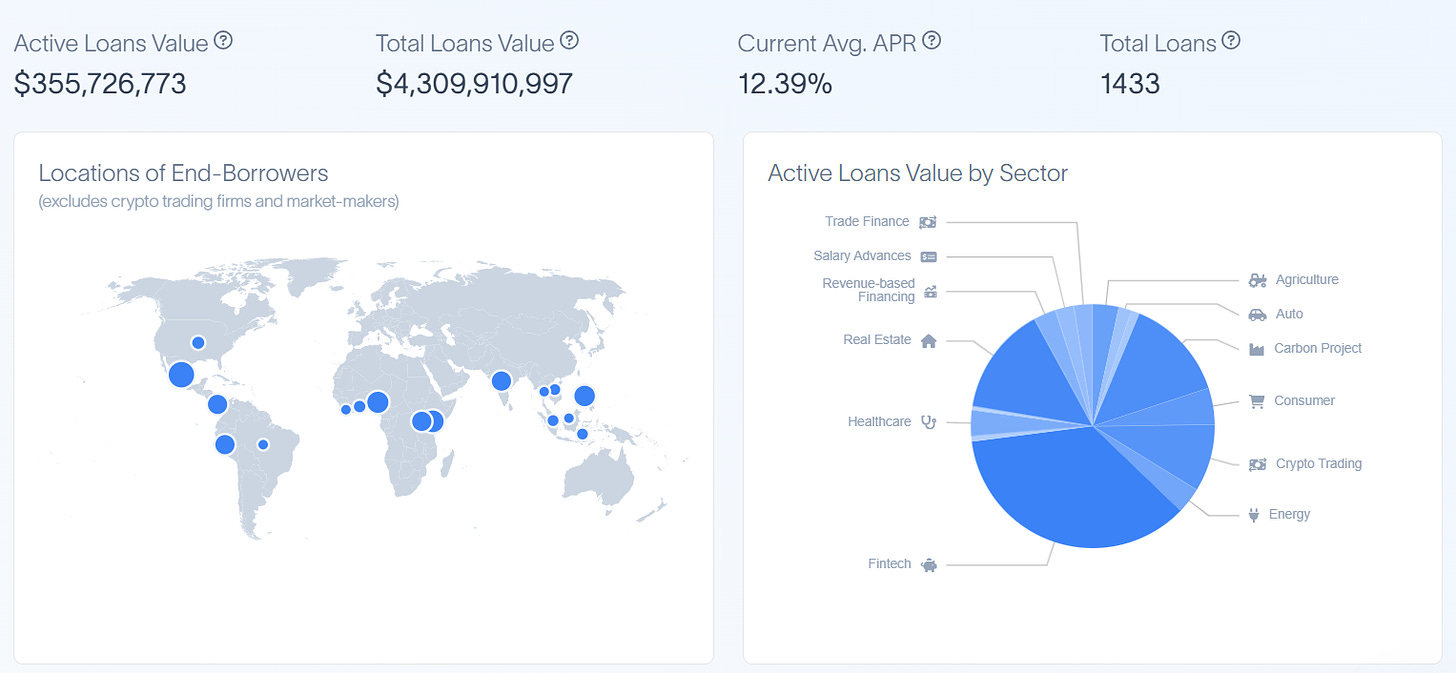
While stablecoins are a growing space and will continue to enjoy demand as users desire on-chain ways to quickly enter and exit into less volatile assets, they will not be the only form of real world asset that gets brought on-chain. Another burgeoning area is the use of DeFi to finance real world credit. In line with the idea that crypto rails offer an efficient way for resource aggregation, a variety of real world lending protocols have arisen. Typically, users can deposit into pools that are managed by KYCed entities, which then use those funds to provide real world loans. The yield from these loans is then distributed back to pool depositors, with defaults being socialized. Loans have ranged from standard loans to crypto market makers for inventory to SMEs in Africa to payment advances for gig economy workers. Key players in this space include Maple Finance, Goldfinch, Truefi, Ribbon Lend, Centrifuge, Credix, and, more recently, MakerDAO.
Summary of private credit powered by DeFi. Credit: RWA.xyz
Going forward, we can expect more and more assets to come on-chain, largely as a result of composability and lower frictions. From mortgages to money market fund shares, there appears to be a vested interest in this convergence of DeFi with traditional finance. One current example of this is Ondo, which has enabled on-chain investing in bond funds for treasuries, investment-grade, and high-yield bonds. The space will no doubt face volatility due to an uncertain regulatory environment but still has immense growth prospects. I believe that more esoteric assets will make their way on-chain first- things like litigation financing- and I’m excited to see how such assets benefit from the broader DeFi ecosystem.
While a lot of institutional interest and capital has fled from DeFi, there still remains a significant amount. In line with this, and in line with the convergence of DeFi and CeFi markets, we will see an increasing amount of RWA on-chain. However, for the upcoming cycle, this will be limited to either very safe assets (i.e. treasuries) or very long-tail assets and will see limited benefits from composability due to KYC/AML rules and shaky regulatory environments.
--------------------------------------------------------------------------------------------------
Zero-Knowledge Infrastructure
Perhaps one of the best byproducts of the bull market was the influx of interest and funding to technologies built on and for zero-knowledge (ZKPs). Often regarded as moon math, ZKPs offer a powerful cryptographic tool that enables the verification of some computation without revealing details about the inputs. In practice, ZKPs offer a few powerful properties to crypto.
ZKPs paired with an execution layer allow for instant finality and succinctness and, in some cases, privacy. Solutions such as Starkware and zkSync are building zkRollups that generate a ZKP for batches of sequenced transactions that can then be submitted to a settlement layer. As opposed to optimistic rollups, which have a week until finality due to the challenge period, ZKPs are final as soon as they are accepted by the settlement layer. Generating ZKPs can be expensive, but they are usually quickly verifiable. Thanks to their privacy-preserving properties, ZKPs can also be used to have pre-confirmation privacy; that is, obscure transactions before they even hit the sequencer such that extracting MEV is significantly harder. However, this involves additional circuitry that can make proofs even more expensive and complex. Nonetheless, whether it originates from succinctness or privacy properties, it is highly likely ZKPs will dominate execution layers in the future. Key players are those mentioned in the section on execution layers: Scroll, zkSync, Starkware, Aztec, and Polygon
In a similar vein to the above, ZKPs allow users to generate proofs over general computations done over network state, which can be thought of as a powerfully secure API layer for blockchains. For example, a prover who wants to bridge an asset from Chain A to Chain B generates a ZKP that the asset was submitted to the bridge contract on Chain A to Chain B, which can then verify this and mint the asset on Chain B (in lieu of a validator committee). Similarly, generating proofs for oracles based on chain data can be done using ZKPs. The utility of being able to prove something about a chain’s state is immense and will be used for the use cases above and much, much more. Some key players in this space include Succinct Labs, Herodotus, and Axiom.
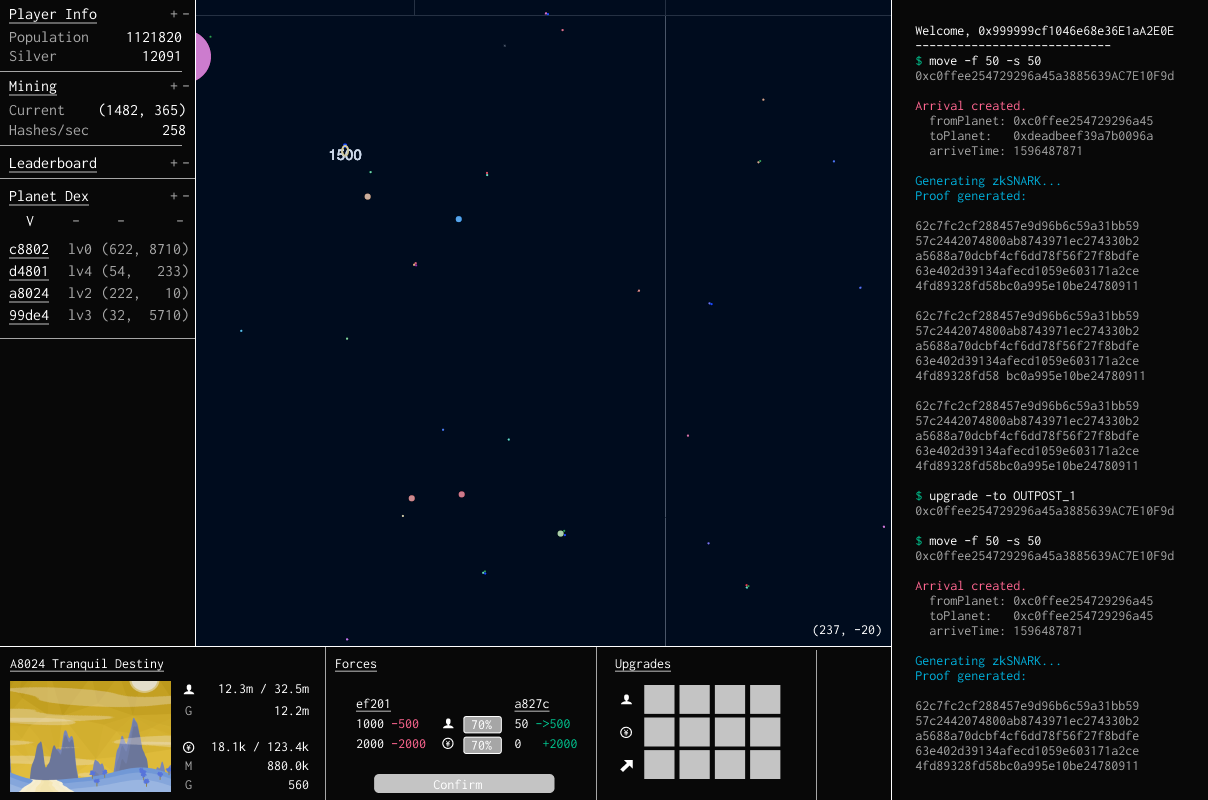
ZKPs also allow for information asymmetry, thanks to the knowledge of inputs being obscured. Many applications will benefit from the information asymmetry provided by ZKPs. In practice, we have seen this most implemented in gaming. Games like Dark Forest use ZKPs to verify that game moves are valid and advance state on-chain without broadcasting information about player coordinates, which would ruin the balance of the game. As such, they end up being a necessary toolbox for any on-chain game or similar application. Key players here are Dark Forest and Cartridge. Geometry Research also published a fantastic implementation of mental poker implemented via zk-SNARKS.
A screenshot of Dark Forest, with the console showing proof generation of moves on the side
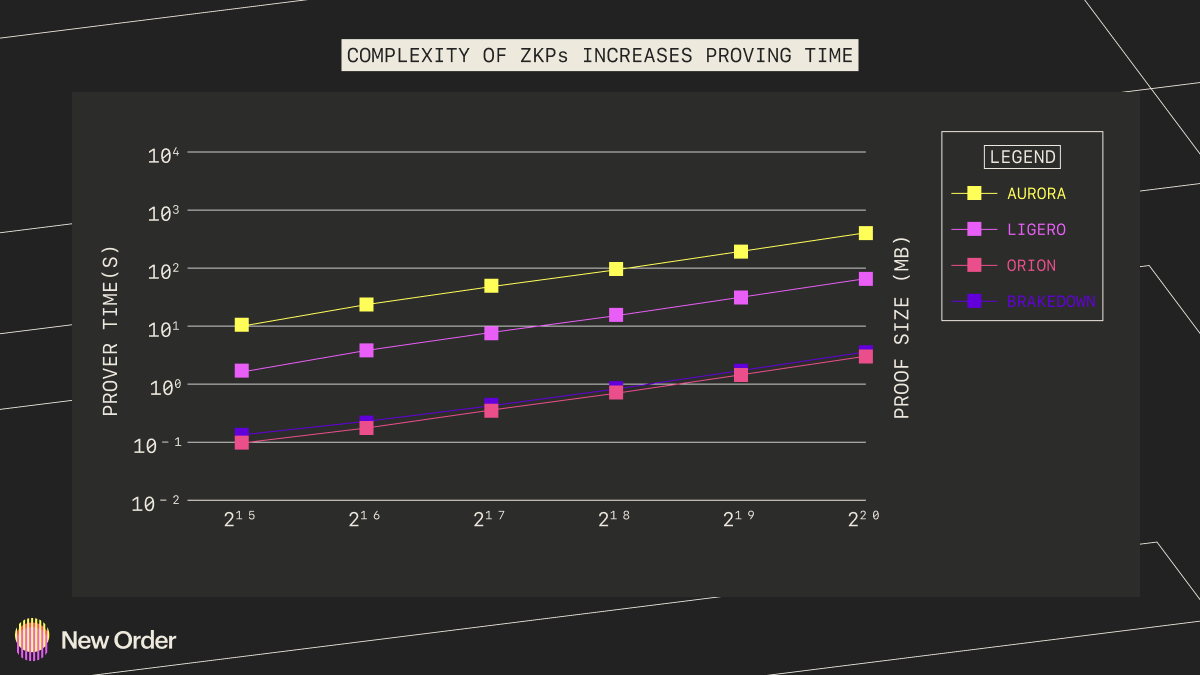
The final, and perhaps most critical point to touch on is the infrastructure around ZKP generation. In particular, specialized hardware for accelerating proof generation will become necessary in the same way that ASICs came to dominate Bitcoin mining. Generating zero-knowledge proofs, especially very large proofs, is an expensive and time intensive task that bottlenecks practical use cases. Until proof generation times are lowered, it is likely that zkRollups will not see meaningful adoption.
Most proving schemes run in O(N). Graphic Credit: New Order Dao, Data Credit: Xie et al.
In what is a gross oversimplification, ZKPs typically make use of elliptic curve pairings to obscure inputs due to their compatibility with quadratic equations. These usually entail a TON of multiplications over elliptic curves with finite fields (which works very differently than traditional multiplication) as well as polynomial interpolation to get to a format that proof systems can understand. For the former, multi-scalar multiplication (MSM) is used and for the latter, we typically see Fast Fourier Transforms (FFTs) applied. MSM, while parallelizable, is incredibly slow and computationally intensive, while FFTs require a lot of memory bandwidth. As such, it is expected that specialized hardware, likely in the form of FPGAs, will come to be used to accelerate ZKP generation. Key players in this space include Ingonayama, Supranational, Ulvetanna, and DZK.
Ultimately, ZK is here to stay but remains burdened by deep technical challenges that limit its commercial viability in the short term. Growth in ecosystems like Starkware is promising, but until proving times are increased via hardware acceleration and advances elsewhere (like proof recursion), other types of execution layers will remain popular. The topic of prover decentralization is also an open question that has seen limited public discourse and success and will remain a key determinant in the in-practice liveness of ecosystems. In the interim, middleware ZK solutions like Herodotus and Succinct will see usage due to their more narrow application scope and non-hardware workarounds to efficiency (i.e. storing Merkle mountain ranges of chain state to lower the time to prove things hidden deep in the state).
--------------------------------------------------------------------------------------------------
Robust Identity Primitives
One of crypto’s core promises has always been the benefit of pseudonymity- a promise that it has mostly fulfilled.
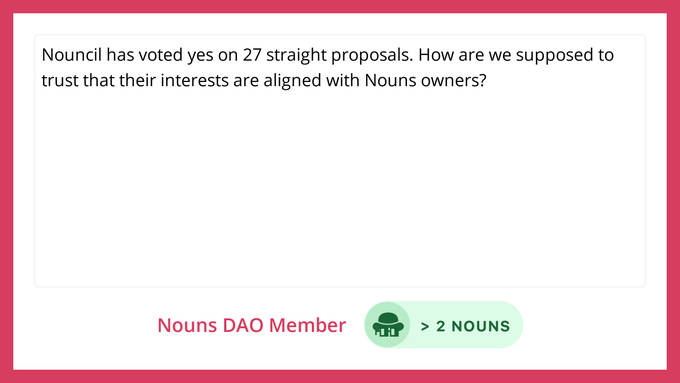
Addresses as abstractions for on-chain identity along with services like ENS allow users to identify themselves as much or as little as possible. Unfortunately, this also comes with drawbacks. Because identity gets atomized across different addresses, it’s difficult to verifiably prove that the individual behind one address is the same one behind another. In a similar vein, a large stakeholder in a protocol may wish to engage in governance anonymously, without doxxing their address or revealing asset ownership balances. The same problem also exists in trying to anonymously prove membership of a group/set or when a user wants to link additional information to their identity that impacts their usage of protocols. In particular, things like bringing real world biometric data on-chain have long been difficult without doxxing sensitive personal information. In order to realize all of these, it is necessary that cryptographic primitives are used for identity attestation, most likely ZKPs. The key players in this space are Personae Labs, BrightID, Quadrata, and to a somewhat lesser extent, Worldcoin.
An example of HeyAnoun, a tool developed by Personae that enables anonymous feedback for NounsDAO.
The other component is robust attribution of on-chain activity. We briefly discussed before how independent auditors might benefit from reputation scoring mechanisms attached and codified on-chain; the same goes for items like credit scoring, governance engagement, and more. Such data would be immensely useful going forward for everything from improving the capital efficiency available to a user to deciding what governance participants are best to delegate to. Some key players in this space are Spectral and ArcX for credit scoring, Rabbithole and Layer3 for on-chain resumes, and Disco for linking social identities on-chain.
Identity is ultimately a core piece of infrastructure that is incomplete in the crypto stack, and I’m excited to see more primitives around identity built. But identity does face one major issue: developing sustainable revenue models linked to pure identity primitives is difficult, which might lower the incentive for builders. To this end, I expect identity focused on specific use cases closer to capital flows (i.e. credit scoring or anonymous KYC) to be the first to be widely used, as the added benefit there is more easily defined (i.e. capital efficiency). It’s unlikely we’ll witness strong demand for general-purpose identity primitives until the next bull market.
--------------------------------------------------------------------------------------------------
Maturation of DAO Governance
Most protocols inevitably tend toward being governed by tokenholders via DAOs. And yet, DAOs remain relatively unrefined in their implementation. Most DAOs exist as direct democracies that vote on everything, without any specialization. While this helps curtail the principal-agent problem, it comes at the cost of being agile, nimble, and having specialized areas. There are a few examples of where DAO governance has actually succeeded in implementing measures for the long term such as Uniswap, Compound, MakerDAO, and Osmosis. Of those, Uniswap tends to have very little to govern, while MakerDAO and Osmosis have relatively concentrated voting power that makes coordination easier. Compound has opted to contract firms like Gauntlet and OpenZeppelin to handle highly granularized governance matters, such as risk parameter tuning. These DAOs work because the products found early product-market fit and had very little that needed to be done by way of governance.
There have been several attempts to solve the tradeoff between the speed of coordination and the principal-agent problem. Optimism, for example, has bicameral governance. Tokenholders vote on treasury management and protocol upgrades, and a separate NFT-gated Citizen’s house voting on public goods funding). Element Finance has the Governance Steering Council, which serves as a pseudo-board of directors that are continuously voted on via delegation block to block. This council has additional governance responsibilities and powers but cannot pass protocol-wide proposals without first consulting with tokenholders. Finally, Metropolis works with protocols like ENS to create Pods: groups focused on governance for specific tasks, like treasury management (akin to departments in a real company). These are all noteworthy experiments that have had varying degrees of success but are still too early in their lifecycle to tell.
An example of Metropolis’ pod system for ENS. Credit: Reverie
Additionally, governance will benefit from platforms that enable voter participation and organization. Beyond the previous section on identity, platforms like Snapshot and Boardroom offer tooling for protocol governance. As governance matures, these will become platforms that are heavily relied on for coordination and user interfacing.
Key companies advancing governance are some of the ones mentioned above: Metropolis, Snapshot, and Boardroom. Additionally, Reverie is an organization that invests in and works with protocols to build effective governance and DAO structures. Finally, there is a lot to be gleaned from traditional corporate governance. Significant research has been done into topics such as the efficacy of having a board of directors and the optimal incentive structure. Mapping these learnings into the world of crypto is an open exploration and one that I will expand on in the near future in a separate piece.
Changes to governance are slow. It becomes very difficult to implement changes to existing governance systems due to both stakeholder apathy and difficulty in reaching a consensus in a timely manner. As such, any changes that do come forth must come from protocols that have yet to establish DAOs to manage the protocols. Given that it takes time for builders and users alike to gradually become comfortable with paradigm shifts in the system they use, meaningful advances will similarly take time and several protocols to successfully implement before they become ubiquitous. This is unlikely to happen for most of this upcoming bear market, and will likely only happen at the tail end. On the longer horizon, I am confident that these changes will eventually occur, especially as more traditional players accrue influence within the space, and apply standard modes of corporate governance to these organizations. Terminally, I expect on-chain governance to become a reflection of standard corporate governance but enshrined in code for added transparency; I believe that the current direct democracy model will become moot.
--------------------------------------------------------------------------------------------------
Decentralized Incentive Networks for Real-World Applications
A very novel byproduct of the recent market was the spillover of crypto applications into the real world beyond private lending. While DeFi dominated the narrative for much of the cycle (hence stablecoins and other RWAs), we also saw the rise of an emergent class of applications that implemented token economies into their systems to incentivize some particular real world behavior. More specifically, I have seen two distinct classes of this emerge which I believe will continue to see outsized growth.
Token economies can be used to build novel physical infrastructure networks. There are several words for this phenomenon, but my favorite is Lattice’s Token Incentivized Physical Infrastructure Network (TIPIN). The core idea between TIPINs is that tokens provide an effective way to incentivize users to contribute capital (financial, human, etc.) in the formation of networks that either build or map physical infrastructure. As an example, Helium gained a lot of popularity in the bull market for its attempt to build a decentralized telecommunications network. By using Helium-compatible technologies, users could create hotspots that rented out extra bandwidth to other users in exchange for Helium’s $HNT token. Users that wanted to use the Helium network to send data would have to burn $HNT to acquire data credits that they would use to pay for data transmission. Helium originally focused on LoRaWAN networks before launching 5G networks that were more consumer-oriented. Today, Helium is embattled by a few controversies that have impacted its efficacy but nonetheless still has just shy of 1 million hotspots across the world. This shows an interesting future in which tokens are on-chain ($HNT was primarily on its own blockchain before a proposal to migrate it to Solana) and are used to incentivize off-chain behavior. The telecom space has proven the most popular for TIPINs so far, but we’ve seen similar companies building for other use cases, including mapping, energy grid management, vehicle data collection, and weather. A few key players focused on telecom include Helium, XNET, Pollen, Meson, and Witness Chain (which is not directly building a TIPIN, but rather a set of cryptographic primitives and tooling for users on the other networks). Other protocols include DIMO for vehicle data, WeatherXM for weather monitoring, HiveMapper for mapping services, and Anode Labs for energy grid management.
An example of a Helium network hotspot providing coverage to other nodes.
Token economies provide effective tools to promote customer brand loyalty. While token economies provide a potent tool to bootstrap entirely novel networks, they also are powerful tools to replace existing brand management. This goes back to the idea that one of crypto’s core competencies involves ownership via protocolization. Existing brand platforms typically only extend to digital interaction and limited incentive systems. For example, you might be able to interact with your favorite clothing brand on social media, and they may even have loyalty rewards systems that lead to being able to purchase certain goods or receive certain discounts, but most brands ultimately have very limited options here and media strategies are synonymous. More importantly, actual consumers and users of a brand rarely have an impact on the direction of that brand. The feedback loop provided by media venues is limited in scope and does not allow users to build or contribute to brand value in more tangible ways. In comparison, on-chain token economies provide low-friction ways for brands to implement incentive systems and customized logic around them. Some concrete examples are the aforementioned usage of NFTs by Kith and Nike (via RFTKT) to create custom clothing drops and NFT passes that enable access to more drops, token-gated parties by the FWB DAO, and NounsDAO funding the creation of luxury sunglasses with ETH from its treasury and a Noun. Over time, I expect that we will see the rise of general-purpose, low-code platforms for token economy development that offer plug-and-play solutions to brands of all sizes, as opposed to the brand-specific loyalty engagement we see today. In particular, key players that are already tackling this include Hang, Blackbird for the restaurant industry, and Kalder.
I believe TIPINs will work on a longer time horizon but will take a few years to be realized. At the end of the day, existing physical infrastructure networks have been entrenched and have had time to both properly scale and develop abstractions for end users that TIPINs do away with (i.e. the complexity of having to pay for data usage with Helium versus a subscription to Verizon is far more). For the near future, TIPIN development will largely be technical (focused on bringing these decentralized systems up to par with centralized ones) and will need to invest in services that make the user experience better (i.e. intelligent automated token management systems). Brand loyalty systems built on crypto rails will see far more success over the next cycle, but still, face immediate headwinds from worsening macro conditions and some of the reputational fallout within crypto. This will delay adoption outside of smaller, more luxury markets.
--------------------------------------------------------------------------------------------------
Decentralized Media and Content Creation
This list would certainly not be complete without mentioning the incredible synergies crypto offers media and content creators. This past cycle saw a veritable tsunami of NFT projects, media-focused DAOs, and other experiments that all seemed focused on one question: is it possible to create a legendary brand from decentralized, bottoms-up efforts? From an NFT-gated TV show about stoner cats with an all-star cast (Mila Kunis, Ashton Kutcher, and Chris Rock are just a few of the names, along with crypto’s own Vitalik Buterin) to Yuga Labs’ efforts to build a Web3 Disney around its core Bored Ape Yacht Club and CryptoPunk IP, crypto saw some insane advancements in this space and garnered significant attention from powerful players in traditional media.
A lot of these efforts typically take advantage of NFTs as claims to ownership for the underlying IP and then attempt to build content atop it. Some have been very successful at doing so, creating comic series, merchandise, crowd-generated lore, and even video games on top of the underlying IP. Others have fallen short of their intended goals. In order to get to a future where media can be built from the ground up consistently, there are a couple of problems that need to be tackled.
A poster for the Stoner Cats TV show.
First, and in line with ruminations on DAO governance earlier in this post, many decentralized media projects either suffer from stagnated governance or lack of tangible incentives to build content atop the original IP (i.e. NFT collections). In the future, more efficient modes of governance combined with established playbooks for sustainable incentives of projects must arise. The closest example we have of active governance in media projects is NounsDAO, which has funded Nouns-related experiments in fashion, street art, AR, and more. However, it’s difficult to concretely value the impact of funding such projects (in fact, many are now calling to attention the loose guidelines by which Nouns funds projects). For decentralized media projects to work, they will need to have more rigid guidelines around project execution, accountability, and performance-based compensation, along with timelines and some sort of smaller set of coordinating stakeholders that can help direct strategic vision.
Second, projects must lower the barriers for users to contribute to the development of brands. At the end of the day, it’s unlikely that most stakeholders in decentralized media protocols will have next-level videogame development or animation skills. Instead, projects should clearly define roles that are conducive to growing brand value without requiring heavy skill sets. This could range from bounties on helping arrange and negotiate partnerships with other media brands, to helping manufacture physical goods, to even contributing towards social media posts. I’m also particularly excited about integrations with generative content platforms, specifically generative AI. Products like DALL-E and ChatGPT lower the barrier to generating visual and written media content. Decentralized media projects might even incentivize users to utilize these tools to generate content by creative prompt inputs; essentially, incentivized prompt engineering.
Ultimately, the field for decentralized media projects is wide open and I expect to see at least one reach mainstream (and non-cringe) appeal. However, in order to get there, the issues mentioned prior must first get resolved. I believe that resolving these issues is a function of time, strong core teams, and substantial resources for experimentation. As such, the landscape will favor existing decentralized media projects with large followings or those that are able to raise outside capital. Key players include staples of the NFT community, like Yuga Labs, Azuki, Pudgy Penguins, Nouns, Moonbirds, Doodles, and Sup. Key players working on alternative forms of this thesis involved Bright Moments DAO for art galleries, Mad Realities for short-form shows, Karate for user-owned fighting league, and Animoca across a variety of projects.
However, building a media brand from the ground up is difficult in this day and age, even with the benefits provided by crypto. Compound this with the reputational fallout from recent industry events, and it becomes very difficult for projects to seriously compete in the mainstream. As such, all decentralized media and content projects will inevitably need to reach some agreement or partnership with either a more established player in the media space (i.e. Fox), which will require some compromise and cession of control. Standalone successes will be extremely rare in this cycle until consumer trust and interest are regained.
--------------------------------------------------------------------------------------------------
Conclusion
Before I conclude this piece, I first want to acknowledge that there are several other areas of interest that I did not include but that I still feel are inevitable. In particular, some more powerful trends we can expect are interoperability as a default, changes to MEV order flow market structure, and the continued growth of liquid staking derivatives and other blockspace products. However, these are all areas I personally believe are either well on their way to maturing, or already have dominant protocols advancing them (i.e. Flashbots and SUAVE for decentralized order flow auctions). Hence, I didn’t want to spend too much time detailing these, as people far smarter and more knowledgeable than myself have already done so. I strongly encourage the reader to look into these spaces as well. In particular, I like New Order DAO’s Thesis for understanding decentralized order flow auctions and interoperability as a default; it’s succinct and well-written. I have several more thoughts on DeFi specifically that are omitted from this article, including cross-chain MEV, solutions to liquidity fragmentation, and more that I’ve chosen to leave for a future piece.
Ultimately, this report was written with two objectives in mind: to highlight some of the more specific trends I think will become foundational to crypto becoming more ubiquitous over the next cycle, and to invite feedback and thoughts from the community so that I may sharpen my own thinking/predictions. Most importantly, I hope this report will be useful in inspiring and resonating with builders and researchers who are either actively working on one of these theses or are looking to do so. If it does, I would love to figure out ways to help you in your journey, whether that's product feedback, getting connected to like-minded builders, or chatting with potential funding sources. Please don’t hesitate to reach out to me on Twitter or on Telegram. Lastly, for future pieces (I expect to be writing a lot more in the quiet of the bear market), I would strongly encourage subscribing to Open Alchemy.
In writing this, I had valuable feedback and revisions provided by many collaborators. Thank you to Joe Kendzicky, Jon Geenty, Walden Yan, Jason Kam, Jeff Tong, Virat Talwar, Kevin Britz, Dmitriy Berenzon, and many, many more friends for your valuable time and effort in reviewing this massive piece.
Disclaimer: This report is for educational purposes and is not financial advice. This report does not represent the views or beliefs of any entity that I work with or hold a position in. I may hold a private/or public position in some of the assets mentioned here.